Security officials say worst effects of global cyberattack subsiding, but remain on edge about new attacks

Reporting from Toulouse, France — Four days after the launch of a global ransomware attack, security officials were optimistic that the worst effects were subsiding even as they remained on edge about new attacks and lingering vulnerabilities.
Their sense of anxiety had been stirred by a digital clue unearthed the previous day that seemed to hint at the involvement of North Korea. While any proof remained thin, some security experts began to debate whether the lack of a financial windfall from the digital blackmail scheme was a sign of ineptitude by the culprits who designed the virus or an indication that its real intent was simply to create chaos.
As if anyone needed more reasons to remain on high alert, the group that was responsible for stealing information from a U.S. spy agency that enabled someone to create the “WannaCry” virus warned that they had obtained far more information that would point to similar vulnerabilities in other computing platforms.
For many security experts who have been battling a rising tide of ransomware in recent years, the presumption was that Tuesday was simply a lull in what has become never-ending digital trench warfare.
“The current hiatus is unlikely to be the end,” said Douglas Crawford, a cybersecurity expert at BestVPN.com. “We can expect a bigger and bolder attack to follow in the wake of this one.”
The WannaCry virus appeared on Friday, a weapon built using a vulnerability, known as Eternal Blue, in Microsoft Windows operating systems. The vulnerability was uncovered by the U.S. National Security Agency but stolen by mysterious hackers known as the “Shadow Brokers.” The details of Eternal Blue were released to the public several weeks ago and WannaCry was the built on its foundation.
By Tuesday, the rate of infections had slowed, in large measure thanks to a young security expert, 22-year-old Marcus Hutchins, who uncovered the virus’ mechanism and registered a website that essentially blocked it. Over the weekend, a second variation of the virus emerged, and another security expert, Matt Suiche, chief executive officer and co-founder of a security startup based in Dubai, also registered a site to blunt the second attack.
“It’s worked pretty well,” Suiche said. “It’s stopped more than 50,000 infections.”
Over the weekend, Europol had reported that the original WannaCry virus had infected more than 200,000 computers in 150 countries. Despite the need to pay a $300 ransom in bitcoin, it appeared as of Tuesday afternoon, only $65,000 had been deposited in three accounts associated with the attack.
That was a paltry sum given the widespread impact. That led some security experts to speculate about some of the rather amateurish aspects of the virus. These included the fact that it had a “kill-switch” that allowed it to be blocked so easily, that it used only a handful of bitcoin accounts that could be easily monitored, and that the process of sending the code to decrypt accounts that did pay was not automated.
We can expect a bigger and bolder attack to follow in the wake of this one. The current hiatus is unlikely to be the end.
— Douglas Crawford, a cybersecurity expert
Jeanette Manfra, acting deputy undersecretary for cybersecurity and communications in the National Protections and Programs Directorate, a division within the Department of Homeland Security, said the U.S. has largely escaped the ransomware attack. She briefed reporters on Tuesday.
Manfra said fewer than 10 U.S. entities were affected by the malware attack, which tied up network information and demanded payment. None of the attacks in the U.S. affected crucial operations, and it did not penetrate any federal government operations, crediting that in part to “aggressive” efforts to make sure agencies installed software patches to fix vulnerabilities.
She said the DHS’ information shows that the malware attack started at least partly in phishing attacks, exploiting users to provide information or click on attachments, but was able to spread throughout other networks on its own.
“We have built in a lot of blocking mechanisms… . I think we have really significantly upped our game in the federal government in terms of doing some of these basics.”
The attacks have mostly been tamped down now, she said, but the U.S. is still working with businesses and overseas partners to make sure it stays that way.
Patrick Coughlin, co-founder and chief operating officer of TruStar Technology, wrote in a blog post that the authors of WannaCry hadn’t even really thought about the economics of their blackmail scheme.
“While the data is far from being conclusive on the actual impact of this kind of attack, it’s safe to say there is some nontrivial gap between the business impact and the willingness to pay,” Coughlin said. “What happens to those economics if WannaCry includes some infrastructure to simplify the bitcoin payment process or if the time period before payment increases shrinks from three days to three hours?”
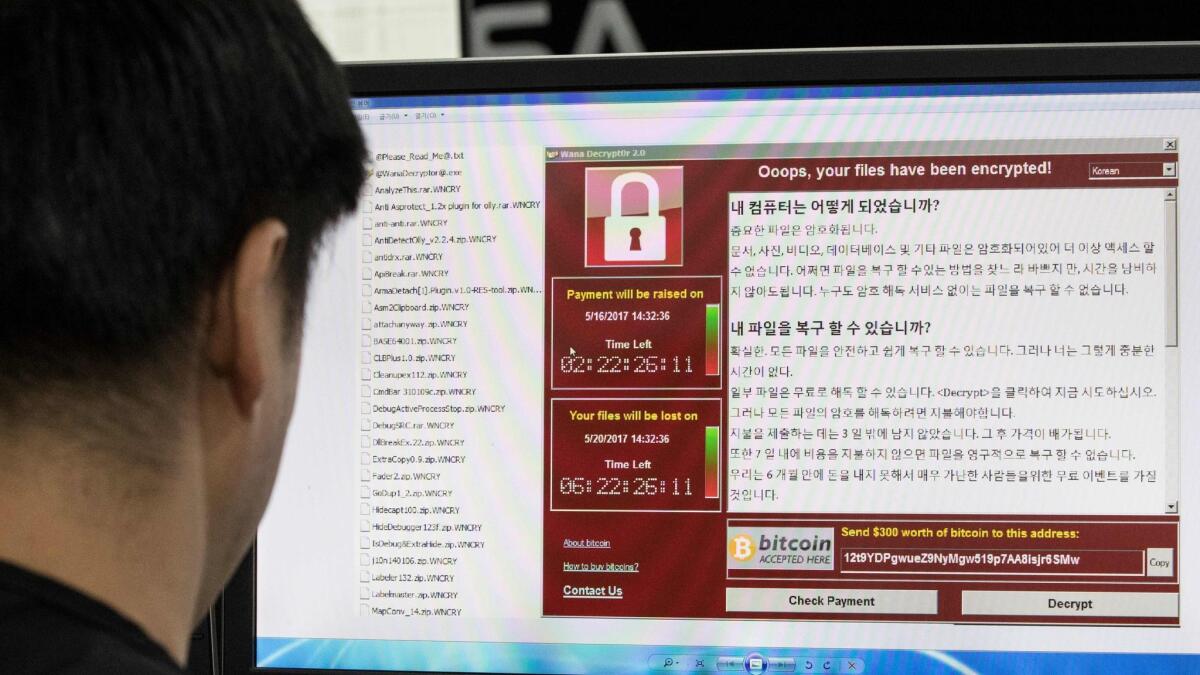
That’s what some researchers found chilling. A more skilled hacker could likely author a more destructive version that exploits the same vulnerability. While Microsoft has issued security patches for Windows software, there are still likely millions of computers around the world that remain wide open to such an attack.
The notion that the attack might have been launched by a nation-state, rather than a rogue criminal group, was no less comforting. Given the tensions between North Korea and the United States this year, the discovery of some code in the WannaCry virus that matched other traces left by a group associated with the hack of Sony Pictures — which many thought was tied to the North Korean government, was disturbing.
While nations like Russia, China or the United States might develop computer viruses for offensive reasons, they typically would build in some sort of limitation out of fear it could run wild and backfire on them. A nation like North Korea, with less valuable infrastructure and much less connected, is seen to be having much less to lose in launching a virus that can wreak indiscriminate destruction.
“This looks more and more like an [operation] designed to create political turmoil,” tweeted Stefan Esser, chief executive of Antid0te, a security startup based on Cologne, Germany.
Security experts also continued to speculate about the role of the Shadow Brokers, the group that released the NSA information. The group appeared to make its first public statement in the wake of the WannaCry attack by posting a large, somewhat unintelligible message on Steemit, a new social networking platform driven by blockchain and cryptocurrency technologies.
In the post, the group mocked Microsoft for that company’s criticism of the NSA and accused the company of secretly working with U.S. government-sponsored hackers. It also said it has possession of other information that pointed to similar vulnerabilities in other computing platforms. However, it didn’t offer specifics.
The group ended its message by saying it was essentially taking the rest of the month of May off. (“In May, No dumps, theshadowbrokers is eating popcorn and watching ‘Your Fired’ and WannaCry.”)
It was not clear if the next part was serious or just a joke, but the group said it would return in June to launch a new “TheShadowBrokers Data Dump of the Month” club that would allow subscribers to get exclusive access to regular releases of stolen material.
“Is being like wine of month club,” they promised. “Each month peoples can be paying membership fee, then getting members only data dump each month. What members doing with data after is up to members.”
O’Brien is a special correspondent. Staff writer Joseph Tanfani contributed to this report.
UPDATES:
2:35 p.m.: This article was updated with comment from the U.S. Department of Homeland Security stating that the U.S. largely escaped the cyberattack.
This article was originally published at 11:30 a.m.
More to Read
Sign up for Essential California
The most important California stories and recommendations in your inbox every morning.
You may occasionally receive promotional content from the Los Angeles Times.











